Scammers Unveil Deceptive New Tactic to Evade iPhone Security Features
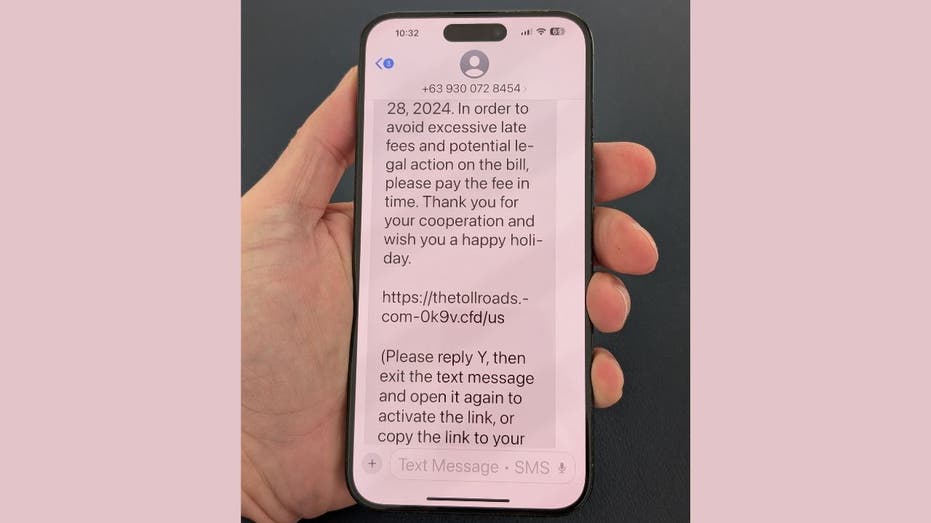
In a concerning turn of events, cybercriminals have developed a cunning method to bypass the built-in phishing protection that Apple provides for iMessage. This new technique potentially exposes users to harmful links and scams, transforming a security feature designed to protect individuals into a vulnerability that can lead to significant personal and financial risks.
Understanding the New Scam Mechanism
Apple’s iMessage includes an automatic feature that disables links in messages received from unknown senders. This is a crucial safety measure aimed at protecting users from phishing attempts. However, scammers have found a way to manipulate this feature. By instructing recipients to respond to their messages—often with a simple “Y”—the attackers can re-enable the previously disabled links. This action not only activates the links but also signals to the scammers that they have an engaged target for future scams.
-
How Facebook Cryptocurrency Ads Are Fueling Dangerous Malware Scams

-
Beware: Popular Chrome VPN Extension Secretly Harvests User Data and Screenshots

-
Australian 3D Printing Robot Charlotte Sets New Standards with Rapid, Sustainable Home Construction

-
Robot dog is making waves with its underwater skills

Defining the Threat: Social Engineering and Smishing
The term “social engineering” refers to targeted attacks that employ impersonation, deception, and manipulation to gain access to personal data. Cybercriminals often disguise themselves as representatives of trusted organizations, using sophisticated techniques to persuade individuals to disclose sensitive information, such as passwords and financial details. Some common tactics include messages that end with instructions like, “(Please reply Y, then exit the SMS, re-open the SMS activation link, or copy the link to open in Safari).”
With the rise of mobile usage for various activities, including financial transactions and personal communications, these smishing (SMS phishing) attacks pose a severe threat to users’ security and privacy.
Essential Steps to Protect Your iPhone and iPad from Malware
To defend against these advanced phishing strategies, consider implementing the following security measures:
1. **Do Not Respond to Suspicious Messages**: Avoid engaging with texts from unknown senders, particularly those asking you to reply to activate links. Delete any suspicious messages and block the sender to prevent future attempts. If you receive a message from an unknown sender, use the “Report Junk” feature to alert your carrier and Apple.
2. **Verify the Sender’s Identity**: If you are uncertain about the legitimacy of a message, contact the organization directly through official channels rather than responding to the text.
3. **Stay Skeptical of Urgent Requests**: Scammers often create a sense of urgency to provoke hasty, unthoughtful reactions. Always take a moment to assess the situation before responding.
4. **Enable Message Filtering**: Utilize your device’s filtering options to manage and sort messages from unknown senders. This feature can help you organize your inbox more effectively and reduce the chances of falling for a scam.
5. **Implement Two-Factor Authentication (2FA)**: Enable 2FA on your accounts. This extra layer of security requires a second form of verification, such as a text message or authentication app, in addition to your password, significantly lowering the risk of unauthorized access.
6. **Install Strong Antivirus Software**: Protect your devices with reliable antivirus software that can detect and block malicious links, alerting you to phishing emails and ransomware threats.
7. **Consider Personal Data Removal Services**: Reducing your online footprint makes it more difficult for cybercriminals to obtain your contact information, thereby decreasing the chances of receiving deceptive iMessage phishing texts.
If You Suspect You’ve Been Targeted
If you believe you’ve fallen victim to a smishing attack, consider leveraging identity theft protection services. Many of these services offer identity theft insurance to cover losses and legal fees, along with dedicated teams to assist in recovering any lost assets.
This recent tactic targeting iMessage users underscores the importance of vigilance, as even secure systems can be vulnerable to social engineering attacks. By remaining cautious and adhering to best practices for digital security, you can significantly mitigate the risks associated with sophisticated phishing attempts.
Engage with Us
What other cybersecurity challenges have you faced with your mobile devices? We welcome your questions and insights—connect with us through our contact page.
For more tech tips and security alerts, subscribe to our newsletter for the latest updates.
Stay informed, stay secure!
